An IT security policy is a protective shield, safeguarding your company's valuable IT assets from threats. Conversely, a weak IT security policy is like a small leak in the roof that, while seemingly inconsequential at first, gradually causes considerable damage. As the leak expands, it becomes increasingly challenging and costly to repair, potentially having catastrophic consequences.
Just as flaws in a roof's structure create cracks for the rain to seep in, inconsistencies in security create vulnerabilities for hackers to exploit. A robust IT security policy protects your organization's data and systems by clearly communicating to employees and customers the security rules they must follow, what activities are prohibited, and who is responsible for what aspects of the security program.
This article will help you develop a comprehensive and easy-to-understand IT security policy to ensure your employees understand and follow the rules and procedures necessary to protect your digital assets.
What Is an IT Security Policy?
An IT security policy is a collection of rules and procedures that protect an organization's data and systems from cyber threats.
A security policy’s primary function is as a guidebook that outlines what's allowed and forbidden in terms of security within the organization. It sets expectations for employees, detailing what they should do, what they should avoid, and their responsibilities.
Security policies can also be customer-facing, requiring them to use strong passwords and two-factor authentication.
IT Security Policy Objectives
An IT security policy focuses on the three core goals of confidentiality, integrity, and availability.
- Confidentiality ensures that only authorized personnel can access data, protecting it from data breaches, leaks, or theft.
- Integrity guarantees that data remains unchanged and uncorrupted while stored, processed, or transmitted within the organization.
- Availability gives authorized individuals access to the resources they need, without disruptions caused by downtime, system failures, or cyber attacks.
Why Is an IT Security Policy Important?
Many industries have laws that require organizations to enforce specific security policies. For example, the healthcare industry must comply with the Health Insurance Portability and Accountability Act (HIPAA), which mandates robust measures to safeguard protected health information (PHI).
Another more universal example is the General Data Protection Regulation (GDPR), one of the world's strictest privacy and security laws, requiring all organizations operating within the EU to protect individuals’ data.
Additionally, operating an organization without a robust IT security policy is risky. You are relying on your employees to self-educate on cyber security and be responsible for regulating their online behavior. This lack of formality significantly increases the organization's exposure to various types of cyber attacks that depend on human error.
On the other hand, organizations with mature IT security policies are 50% less likely to experience a data breach. Furthermore, if a security incident does take place, a mature security policy helps the organization contain the damage and recover quickly.
16 IT Security Policies You Should Consider
Corporate governance in IT security is flexible, allowing for diverse policy structures. A conventional approach is to create a foundational document to outline the security strategy, its encompassing principles, objectives, and responsibilities.
Specific security policies developed from this initial document provide in-depth guidance that focuses on different aspects of security, including data protection, password management, remote access, and incident response. These specific policies combine with the foundational document, forming an integrated framework for IT security.
Here are the 16 essential IT security policies to consider implementing.
1. Acceptable Use Policy
An acceptable use policy (AUP) defines how users can interface with an organization’s computing resources. An AUP aims to protect networks and resources from misuse by informing employees and customers about acceptable behavior and the consequences of potential policy violations.
For example, a customer facing AUP might prohibit customers from posting illegal or copyrighted content on the company's website or from using the company's services to send spam.
On the other hand, an employee facing AUP might prohibit employees from using the company's IT resources to download illegal software.
Importance
AUPs effectively protect against inadvertent lapses of judgment that happen when employees fall prey to social engineering attacks while browsing Facebook on a company device. However, AUPs won't prevent sophisticated threats like spear phishing, which require training to avoid.
Additionally, AUPs are a legal shield if an employee or customer uses a company's resources to violate the law. By explicitly prohibiting illegal activities in the AUP, the company establishes a clear boundary that, if crossed by any user, shifts responsibility away from the organization.
Key Tips
- Use plain and understandable language while avoiding jargon or overly technical terms.
- Keep the AUP concise and focused, covering essential rules without unnecessary complexity.
- Ensure all employees, contractors, and users are aware of the AUP.
- Outline the consequences of violating the AUP, including warnings, temporary suspensions, or even termination of access or employment, depending on the severity of the violation.
2. Security Awareness and Training Policy

Security awareness training teaches individuals to recognize and prevent cyber threats such as ransomware and phishing, and attempts to weave cybersecurity best practices into the very fabric of an organization.
Importance
According to the latest data, 74% of all cybersecurity breaches involved the human element. Security awareness training creates a human firewall shielding your organization against hackers seeking to exploit untrained and naive individuals, the most vulnerable link in any network.
Key Tips
- Outline the objectives of your training program. What are the specific security goals you aim to achieve through training?
- Customize the training to address your organization's risks, challenges, and industry-specific compliance requirements.
- Determine which employees require specialized training based on their roles or access to sensitive data.
- Ensure that the policy includes provisions for regular updates to training materials and content to keep pace with evolving threats.
- Design training modules that are engaging and interactive. Use real-world scenarios, quizzes, and practical exercises to make learning more effective.
3. Change Management Policy
A change management policy is a set of procedures organizations use to manage changes. In IT security, a change management policy ensures that any alteration to IT infrastructure and processes is well-documented, reviewed, and implemented systematically.
Importance
Suppose a company wants to enhance its network security by implementing new technologies which require adjustments to existing infrastructure like the firewall and intrusion detection system. Without a structured policy, the IT team will deploy the solution without adequate planning or testing. The result of this rushed approach is that the new solution clashes with existing systems, causing disruptions, performance issues, and introduces vulnerabilities into the network.
However, with a change management policy, the IT team would follow a systematic process. Initially, they assess how the new solution impacts the company's network and existing systems. Then, they create a deployment plan encompassing testing, gradual implementation, and continuous monitoring after deployment.
Key Tips
- Clearly define the roles and responsibilities of employees involved in the change management process.
- Implement a standardized change request form or system for documenting and tracking changes.
- Establish a rigorous change approval process with multiple levels of review.
- Conduct impact assessments to understand how changes may affect other systems or processes.
- Communicate changes to relevant stakeholders and ensure proper testing and rollback plans are in place.
4. Incident Response Policy
An incident response policy is a set of procedures that streamline the way an organization responds to and manages security incidents or data breaches. It outlines the steps to detect, analyze, mitigate, and recover from incidents in a structured and coordinated manner.
Importance
An Incident Response Policy saves time, reduces confusion, and minimizes damage during a security incident. Without it, you risk chaotic, uncoordinated responses that can exacerbate the problem.
Key Tips
- Clearly define what constitutes a security incident and classify them based on severity.
- Establish an incident response team with designated roles and responsibilities.
- Develop incident response plans and playbooks for various types of incidents.
- Train employees on how to recognize and report incidents.
- Continuously update and test the incident response procedures to ensure they are effective.
5. Remote Access Policy
A Remote Access Policy governs how employees remotely connect to an organization's internal network, systems, or data.
Importance
IBM's 2020 Cost of a Data Breach Report vividly illustrates the consequences of organizations suddenly being compelled to transition to remote work.
Among the organizations that adopted remote work due to COVID-19, 76% reported it took them longer to identify and mitigate data breaches. Subsequently, remote work resulted in an uptick of nearly $137,000 in the average cost of a data breach.
With remote work here to stay, having a comprehensive remote access policy is crucial for maintaining network security.
Key Tips
- Employ strong authentication methods, such as two-factor authentication (2FA).
- Implement in-transit encryption for data sent over remote connections.
- Educate remote users on secure remote access best practices, such as avoiding public WiFi networks.
6. Vendor Management Policy
A Vendor Management Policy is a set of procedures and guidelines that manage an organization's relationships with third-party vendors and suppliers.
Importance
Cyber criminals are increasingly targeting third-party vendors because they are typically a softer target than the organization they are preying on. Additionally, vendors often have access to sensitive data from multiple clients, meaning a successful breach can have a ripple effect on all the organizations that rely on them.
Recent findings reveal that 98% of organizations worldwide have connections with at least one third-party vendor that has suffered a breach within the past two years. When organizations integrate with third-party vendors that have suffered recent breaches, they inherit those vendors' security vulnerabilities and weaknesses.
Concerningly, vendors are five times more likely to have inadequate security, with half having indirect ties to as many as 200 fourth-party vendors that have previously fallen victim to data breaches.
In many industries, organizations are legally responsible for the security of the data they hand over to third-party vendors. Breaches involving these vendors often lead to non-compliance, legal liabilities, and reputational damage.
Key Tips
- Conduct thorough assessments of your vendors, including their security strategy and incident response plans.
- Communicate your organization's security requirements and expectations to vendors.
- Establish security clauses and requirements in vendor contracts, including service-level agreements (SLAs).
- Continuously monitor vendor security through audits, assessments, and penetration tests.
- Have a contingency plan for vendor-related disruptions, including data breaches or downtime.
Supply chain attacks target the weakest link in the chain, which is often a third-party vendor. A prime example is the infamous Target data breach, in which attackers compromised a third-party vendor, Fazio Mechanical, to gain access to Target's network. This breach was one of the largest in history, resulting in 40 million compromised credit card numbers, addresses, and phone numbers. Target had to pay the victims $18.5 million in settlements.
Explore our article on social engineering examples to learn how to identify and defend against these tactics.
7. Password Creation and Management Policy

A password creation and management policy outlines the rules for creating, using, and maintaining passwords. It typically includes guidelines for password complexity, expiration, and protection.
Importance
Strong passwords are essential for cybersecurity. Even a relatively basic password policy can significantly reduce the risk of data breaches, given that 64% of people reuse the same password on multiple, or sometimes all, accounts. If only one of these accounts is compromised in a data breach, hackers can perform a credential stuffing attack to access all other accounts that use the same password.
By mandating complex and unique passwords, you eliminate easily exploitable vulnerabilities hackers love to exploit.
Key Tips
- Require complex passwords at least 12 characters long with a mix of letters, numbers, and special characters.
- Urge employees not to reuse passwords.
- Implement password expiration and mandate regular password changes.
- Encourage the use of password managers.
- Prohibit password sharing and storing passwords in insecure locations.
8. Network Security Policy
A network security policy is a set of safeguards that prevent unauthorized access to an organization’s computer network. It includes hardware and software solutions such as email security systems, firewalls, intrusion detection systems, and virtual private networks (VPNs).
Importance
Network security is the first line of defense against DDoS attacks, spyware, insider threats, and advanced persistent threats (APTs).
By preventing security breaches, robust network security also helps businesses save money and improve efficiency.
Key Tips
- Regularly update and patch network devices and software to patch up the vulnerabilities that attackers could exploit.
- Invest in network monitoring and intrusion detection systems to automate responding to threats.
- Employ network segmentation by dividing your IT infrastructure into smaller subsystems, each with independent security controls, preventing attackers from quickly moving between segments in case of a breach.
- Create honeypots or fake subnetworks to deceive and trap hackers. Honeypots imitate genuine systems while intentionally incorporating vulnerabilities. As legitimate users do not access them, any activity signals third-party intrusion.
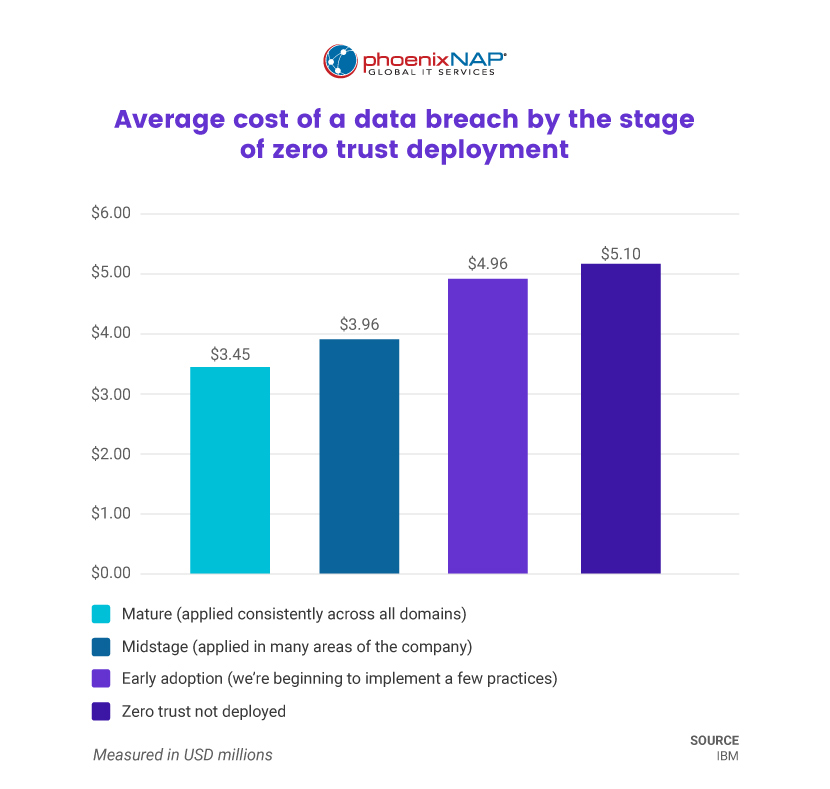
Zero Trust is a security strategy that assumes no implicit trust for any user or device inside or outside the network perimeter. Instead, it verifies every user and device before granting access. To learn more about zero-trust security, read our in-depth article.
9. Access Authorization, Modification, and Identity Access Management
This policy governs the rules for granting, changing, and managing user access to the organization's systems and data. It covers user provisioning, role-based access control, and identity management.
Importance
Effective access management is essential for protecting the organization from unauthorized access. Organizations greatly reduce the risk of breaches and incidents by ensuring that users only have the permissions they need to perform their job duties.
For example, a customer support agent should not have access to financial databases because they do not need this information to do their job. Granting unnecessary access, irrespective of the employee's department or position, could lead to accidental or deliberate breaches of customer privacy, data protection regulations, and overall security.
Key Tips
- Implement role-based access control (RBAC) to assign permissions based on job roles.
- Conduct regular access reviews to ensure access permissions remain appropriate.
- Automate user provisioning and de-provisioning processes.
- Integrate identity and access management (IAM) solutions for centralized control.
10. Data Retention Policy
A data retention policy defines how long an organization keeps data and when and how they dispose of it.
Importance
Many industries mandate organizations to retain certain types of data for a specified period. Failure to comply can result in fines and penalties.
Data retention policies are also beneficial for legal reasons. For example, an organization may need to produce electronic records as evidence in court. If the organization does not employ robust data retention, it may be unable to produce the necessary records, which could result in them losing the case.
Additionally, stored data can inform marketing decisions and enable a business to track trends and identify improvement areas.
Key Tips
- Not all data is created equal – some is highly sensitive and must be retained longer. Classifying will help you develop a tailored policy that meets your needs without wasting resources.
- Once you have classified your data, you must assign retention periods based on the risk and relevant compliance requirements. For example, you need to retain financial data for seven years to comply with SEC regulations.
- Educating your employees on data retention rules will ensure that the policy is effective and your data protected.
- Consider leveraging automated data archiving and disposal to save time and resources.
11. Mobile Device Management (MDM) Policy
A mobile device management policy defines how an organization manages and secures mobile devices like smartphones and tablets.
Importance
Mobile devices have become an essential part of the workplace, with 87% of employees using them to access company apps, personal messaging, and email.
However, mobile devices pose unique security risks. They are frequently lost or stolen, giving attackers access to sensitive data. Mobile devices are also more vulnerable to malicious apps, which steal data, infect the device with malware, or take complete control.
Another significant vulnerability of mobile devices is that people often use them on unsecured public WiFi, which hackers exploit to intercept data transmitted between the mobile device and the company network.
Key Tips
- Mandate strong passwords and two-factor authentication to protect devices from unauthorized access.
- Remotely wipe lost or stolen devices.
- Specify which apps and websites are allowed, and only allow employees access to data they need for their jobs.
- Regularly update mobile device security settings and software to fix known vulnerabilities.
12. Bring Your Own Device (BYOD) Policy
A BYOD Policy outlines how employees can use their personal devices for work, whether in the office or from home. Smartphones are the most common devices used in BYOD, but employees may also use tablets, laptops, and PCs.
Importance
Some employees will inevitably connect to the corporate network with personal devices, regardless of whether the company has a BYOD policy. Organizations should either ban personal devices for work-related tasks or create a BYOD policy to mitigate this risk.
BYOD policies allow organizations to improve employee satisfaction, reduce hardware and software costs, and speed up turnarounds and onboarding processes.
However, there are also notable drawbacks to allowing employees to work from personal devices, the biggest of which is security. BYOD grants access to business apps and resources to unmanaged devices, creating a broad attack surface for hackers to exploit.
Key Tips
- Before creating a BYOD policy, talk with your employees to ensure that they understand BYOD and that they have devices that meet your security requirements. Inform them that BYOD will require some degree of control over their devices.
- Define which types of personal devices are allowed and provide guidelines for their use. For example, you may allow iPads but forbid other tablets due to security concerns. You may also limit devices based on brands and operating systems, but a more cautious approach is to specify allowed models and versions.
- Create a list of permitted and banned apps for all devices connected to your network, including corporate and personal devices.
- Mandate security measures like device encryption, strong passwords, two-factor authentication, and remote wiping.
- The BYOD policy must include an acceptable use policy and offboarding procedures for employee-owned devices. The most secure offboarding strategy is a mandatory, complete wipe of the device, but first, ensure that employees have backed up personal data.
13. Encryption and Decryption Policy
Encryption and decryption work by transforming data into an unreadable form using a secret key and then reversing the process using the same or a different key. Decryption and encryption policies are the rules that govern how, when, and who performs encryption, whether data is at rest or in transit.
Importance
Without strong encryption, your data is vulnerable to theft and unauthorized access by hackers. On the other hand, if cyber criminals steal your encrypted data and don't have the key, they would have to decrypt it by brute force, trying every possible combination of keys until they find the correct one.
Many industries have regulations that mandate the encryption of sensitive data. For example, not encrypting protected health information in the healthcare industry will make you non-compliant with HIPAA and liable to fines and penalties.
Key Tips
- Many different encryption algorithms are available, each with its strengths and weaknesses. Choose an encryption algorithm appropriate for the sensitivity of the data you protect and the available resources.
- Implement strong key management practices to protect your encryption keys. If they fall into the wrong hands, your data is at risk.
- Ensure that encryption is applied consistently across all relevant systems and devices.
14. SPAM Protection Policy
Spam is any unwanted electronic communication, including email, text messages, and social media posts. It is often used to promote products or services, but hackers can also use it to spread malware or conduct phishing attacks. A spam protection policy outlines the procedures for blocking spam through email filtering, anti-phishing measures, and user awareness.
Importance
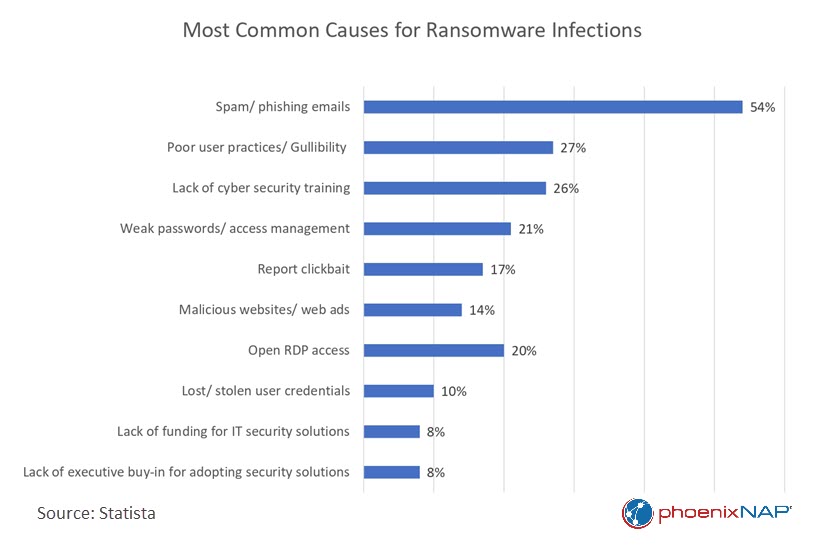
Spam and phishing emails are a major threat to businesses of all sizes. In 2022, spam accounted for nearly 49% of all emails sent, up from 46% in 2021. The most common type of phishing scam was bulk phishing, with around 85% of companies worldwide experiencing it.
Hackers use spam and phishing emails to deliver malware, steal sensitive information, or initiate cyber attacks. For example, a phishing email may contain a link that, when clicked, downloads malware onto the victim's computer. Alternatively, the email may ask the victim to enter their personal information, such as their password or credit card number, on a fake website.
A robust spam protection policy can help to reduce these risks.
Key Tips
- Use a spam filter to identify and block spam emails.
- Monitor email traffic for suspicious activity, such as many emails being sent from a single IP address.
- Educate employees about spam and phishing attacks so they know what to do if they receive one.
- Block known spam senders at the network level to prevent spam emails from reaching employee inboxes.
15. System Maintenance Policy
A System Maintenance Policy outlines the procedures and schedules for maintaining and updating an organization's IT infrastructure, including hardware, software, and backups.
Importance
Maintenance is essential for ensuring a computer system's smooth and secure operation. By identifying and resolving potential problems before they cause issues, system maintenance policies can help reduce the risk of downtime and improve performance, reliability, and lifespan.
Key Tips
- Schedule routine maintenance to minimize disruption to operations.
- Document tasks and maintain a to-do list to ensure that maintenance tasks are consistently performed.
- Assign maintenance tasks to specific personnel to prevent them from being overlooked or forgotten.
- Develop a comprehensive system backup and disaster recovery plan.
16. Vulnerability Management Policy
Security vulnerabilities are weaknesses companies have failed to patch on time. Although these weaknesses may be small and easy to overlook, they can provide a backdoor for hackers to slip in undetected.
A vulnerability management policy outlines the processes and responsibilities for systematically identifying, assessing, and remediating vulnerabilities in an organization's IT environment.
Importance
If your vulnerability management is working, you will not see it directly because vulnerabilities will have been preemptively identified and patched. You will, however, indirectly see the benefits of vulnerability management in the form of a more secure system and a reduced risk of security breaches.
Key Tips
- Perform regular vulnerability scanning and assessment.
- Prioritize vulnerabilities based on severity and potential impact.
- Establish a patch management process to apply security updates promptly.
- Conduct risk assessments to determine the impact of unaddressed vulnerabilities.
How to Write an IT Security Policy?

Here's a simplified guide on how to write an effective IT security policy, along with what it should include:
1. Define the Purpose and Scope
Begin by establishing why you need this policy and who it applies to. Is it for employees, contractors, or other stakeholders? Specify the scope to set clear boundaries.
2. Identify Key Stakeholders
Determine who will create, review, and enforce the policy. This might include IT professionals, legal experts, HR, and management.
3. Assess Risks and Requirements
Identify the specific security risks your organization faces. Consider industry regulations and compliance requirements, such as HIPAA, GDPR, or PCI.
4. Establish Guidelines and Procedures
Under each policy statement, provide detailed guidelines and procedures that outline how employees should comply. Be specific about actions, responsibilities, and best practices.
5. Outline the Consequences
Specify the disciplinary actions and legal consequences of policy violations.
6. Approval and Distribution
Once the policy is complete, seek approval from senior management or the appropriate authority. Distribute the policy to all relevant stakeholders.
7. Review and Revision
Annually review and update the policy to adapt to evolving threats, organizational changes, and new regulations.
8. Document Everything
Keep thorough records of policy development, revisions, training, incidents, and enforcement actions.
Our PCI hosting and HIPAA-ready hosting are secure by design and built to meet the most rigorous privacy requirements. With strong encryption, stringent access controls, and comprehensive data backup and recovery capabilities, we offer unparalleled protection of sensitive data.
How to Implement and Enforce an IT Security Policy?
Processes and procedures are the pillars of any organization. However, their effectiveness hinges on proper execution and consistent enforcement.
Here are some guiding principles of effective policy in the workplace.
1. Clear Communication
Communicate policies and procedures clearly, explaining the purpose, benefits, and expectations. Use a variety of channels and formats, and make sure they are accessible and regularly updated.
2. Training and Support
Provide employees with the resources, tools, and guidance they need to adhere to policies and procedures. Create a culture of learning and improvement where employees can share best practices, seek assistance, and receive constructive feedback. Recognize and reward adherence to security practices.
3. Monitoring and Review
Monitor and evaluate policy implementation and effectiveness regularly. Identify gaps, issues, or opportunities for improvement. Engage employees in this process by inviting feedback and questions.
4. Correction and Prevention
Address violations and deviations promptly, consistently, and proportionately. Communicate consequences and expectations. Analyze root causes and implement preventive measures.
5. Leading by Example
Model the behaviors and attitudes you expect from employees. Empower and encourage them to take ownership of compliance. Foster a positive and respectful work environment where employees feel valued, trusted, and supported.
IT Security: From Policy to Practice

An IT Security Policy is the custodian of an organization's culture, reflecting its values and perspectives regarding information. It's not a one-size-fits-all document but a carefully curated and dynamic indicator of how a company views risk and values data. This individuality is precisely why generic boilerplate policies often fall short of capturing the intricacies of each organization's operations.
At its core, the IT security policy's mission is clear – to safeguard the confidentiality, integrity, and availability of systems and data. As such, it's a guiding light, not a roadblock, designed to support an organization's productivity and innovation.